Tips for Secure Online Shopping
In today’s digital age, online shopping has become a common and convenient...
Understanding and Avoiding Malware: A Comprehensive Guide
In today’s digital world, malware is a pervasive threat that can cause...
Keeping Your Social Media Accounts Secure: A Comprehensive Guide
In today’s digital age, social media accounts are more than just platforms...
The Importance of Backup and Recovery
In an era where digital data is the lifeblood of organizations and...
Protecting Your Home Network: A Comprehensive Guide
In an age where our lives are deeply intertwined with digital technology,...
Secure File Sharing Practices: Ensuring Data Safety in a Digital World
In today’s interconnected world, file sharing has become an integral part of...
How to Spot Fake Websites: A Comprehensive Guide
In today’s digital age, the internet offers endless opportunities for learning, shopping,...
The Role of Firewalls in Cyber Security
Introduction Firewalls play a pivotal role in modern cyber security, acting as...
Safe Email Practices: Ensuring Security in Personal and Professional Communication
In an age where email remains a primary mode of communication, ensuring...
Protecting Against Social Engineering Attacks: A Comprehensive Guide
Social engineering attacks exploit human psychology rather than technological vulnerabilities to gain...
Managing and Securing Personal Information Online
In an increasingly digital world, managing and securing personal information online has...
Securing Mobile Devices: A Comprehensive Guide
In our increasingly digital world, mobile devices such as smartphones and tablets...
Understanding and Avoiding Ransomware: A Comprehensive Guide
Introduction to Ransomware Ransomware is a form of malicious software designed to...
Using VPNs for Enhanced Privacy
In today’s digital landscape, where data privacy is a growing concern, Virtual...
How to Secure Your Wi-Fi Network: A Comprehensive Guide
In today’s connected world, securing your Wi-Fi network is crucial to protect...
Recognizing Phishing Scams: A Comprehensive Guide
Phishing scams are deceptive attempts to gain sensitive information by disguising as...
Safe Browsing Habits: A Comprehensive Guide
In today’s digital age, browsing the web safely is more important than...
Two-Factor Authentication (2FA) Benefits: A Comprehensive Overview
In an age where cyber threats are increasingly sophisticated and pervasive, securing...
Best Practices for Strong Password Creation
In today’s digital age, strong passwords are fundamental to safeguarding personal and...
The Importance of Regular Software Updates
In today’s fast-paced digital world, keeping software up-to-date is more crucial than...
Understanding Cyber Security Basics
In an increasingly digital world, understanding cyber security is crucial for protecting...
A step-by-step guide to understanding how to break passwords
Cracking passwords is frequently mentioned as one of the most common types...
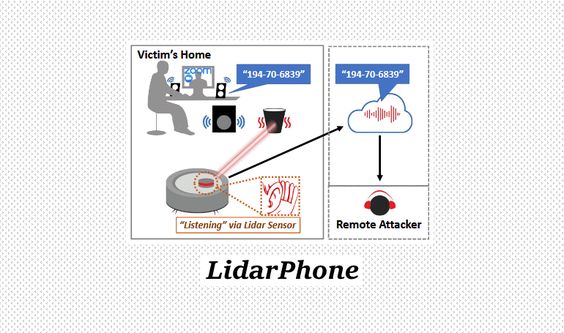
LidarPhone Threat Transforms Smart Vacuums Into Spying Microphones
A laser microphone is a surveillance device that uses a laser beam...
The “Lucky Thirteen” Attack
Software developers are raising to patch a vulnerability that has recently been...
Cloudflare is Introducing Magic Firewall
On 16 October 2020, Cloudflare officially announced the launch of Magic Firewall™,...
How Do You Tell If Your Smartphone Has Been Infected By The Virus
Knowing if your phone has been infected can get tricky, but certain...
6 Steps To Create Stronger Passwords
As your password secures all the tools on your system, such as...
10 Most Important Cyber Security Tips for Your Clients
The internet is now a distance riddled with viruses, trojans and hyperlinks....
How to construct a secure remote working business
The strain has been put by the impact of coronavirus on Businesses...
Does the Bruteforce of PHPSESSID Attack Affect You?
But for an attacker on the prowl. you become an easy target...