Table of Contents
![]()
A laser microphone is a surveillance device that uses a laser beam to detect sound vibrations in a remote object. It can be used to eavesdrop with limited exposure.
History of Laser Microphone
The object is usually inside a room where a conversation is taking place and something can vibrate (for example, an image on a wall) in response to the pressure waves produced by the noises in the room. The object should ideally have a smooth surface so that the beam can be correctly reflected. The laser beam is directed through a window to the room, bounces off the target, and returns to the receiver that converts the beam to an audio signal. The beam can also be reflected off the window itself. The minute variations in the distance travelled by the light as reflected by the vibrating object are detected interferometrically. The interferometer translates variations to variations in amplitude, and electronics are used to translate these variations to signals that can be converted back to sound.
The technique of using a light beam to remotely record sound possibly originated with Léon Theremin in the Soviet Union at or before 1947, when the Buran eavesdropping system was developed and used. This worked by using a low-power infrared beam (not a laser) from a distance to detect the sound vibrations in the glass windows. Lavrentiy Beria, head of the KGB, used this Buran device to spy on the U.S., British and French embassies in Moscow.
The U.S.A. on August 25, 2009. Patent 7,580,533 was authorised for a device that uses a laser beam and smoke or vapour to detect sound vibrations in free air (“Particulate Flow Detection Microphone based on a laser-photocell pair with a moving stream of smoke or vapour in the laser beam’s path”). Sound pressure waves cause smoke disturbances which in turn cause variations in the amount of laser light reaching the photodetector. A prototype of the system was exhibited at the 127th Audio Engineering Society convention in New York City from 9 to 12 October 2009.
The same basic definition was adopted by academics from the University of Maryland and the National University of Singapore but applied it to the Xiaomi Roborock vacuum cleaner.
Such requirements must be met
The assault on LidarPhone is not easy, and some criteria need to be met. For instance, an intruder will need to use malware or a corrupted update process to change the vacuum firmware to take control of the LiDAR portion.
This is required because vacuum LiDARs operate by rotating at all times, a process that reduces the number of data points that an intruder may obtain. Via tainted firmware, attackers would need to stop the LiDAR vacuum from spinning and instead concentrate on one nearby object at a time when it could record how its surface vibrates to sound waves.
Besides, given that the Smart Vacuum LiDAR components are nowhere near as reliable as surveillance-grade laser microphones, the researchers also noted that the laser readings obtained will need to be uploaded to the remote server of the attacker for further processing to improve the signal and bring sound quality to a state where it can be understood by a human observer.
Despite all these conditions, however, researchers have said that they have been successful in recording and obtaining audio data from the LiDAR navigation portion of the Xiaomi robot test.
They tested a LidarPhone attack with a variety of objects, depending on the distance between the robot and the target, and the distance between the source of the sound and the object.
Tests focused on the recovery of numerical values, which the research team said were able to recover with 90 per cent accuracy.
But researchers have proposed that the method may also be used to classify gender-based speakers, or even to assess their political affiliation from the music played during news shows, recorded by the LiDAR vacuum.
There’s no reason to worry. It’s just academic studies.
But while the LidarPhone assault sounds like a gross invasion of privacy, users don’t need to panic for the time being. This form of attack is based on many of the prerequisites that most attacks won’t bother. There are much easier ways to spy on users than overwriting a vacuum firmware to monitor their laser navigation device, such as tricking the user into downloading malware on their phone.
The LidarPhone attack is merely novel academic research that can be used to bolster the security and design of future smart vacuum robots.
The key suggested counter-measure of the research team for smart vacuum cleaner robots is to shut down the LiDAR part if it is not spinning.
So, what do you think about this technology? Tell Supedium your taught about this spying technology🕵️
Share This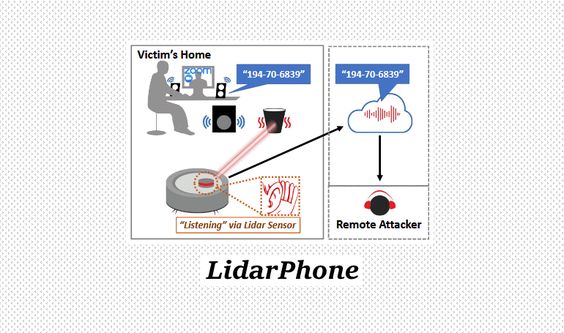




Be the first to comment