![]()
WordPress 5.6, the final major release planned for 2020, comes out today, on December 8, 2020. It includes a few major features and updates, as well as a huge number of minor enhancements and bug fixes. A few changes have immediate implications for security and compatibility which we’ve highlighted in this post for WordPress users.
Application Passwords add functionality, and risk
WordPress 5.6 will come with a new feature that allows external applications to request permission to connect to a site and generate a password specific to that application. Once the application has been granted access, it can perform actions on behalf of a user via the WordPress REST API.
Unfortunately, socially engineering a site administrator into granting application passwords to a malicious application is trivial. An attacker could trick a site owner into clicking a link requesting an application password, naming their malicious application whatever they wanted:
Worse yet, the application password request URLs are set up to send the newly generated password to the requester’s site via a redirect URL. Since application passwords function with the permissions of the user that generated them, an attacker could use this to gain control of a website. We demonstrated how an attacker could use a social engineering attack using application passwords on Wordfence Live.
For this reason, the latest version of Wordfence, 7.4.14, disables application passwords by default. If you have a specific use case for application passwords and would like to re-enable application passwords, you can do so under Wordfence->Firewall->Manage Brute Force Protection:
Despite the risk, application passwords are likely to offer some utility in the future. Some examples of how they could be used include publishing posts to a WordPress site from other interfaces, accessing or updating data in the WordPress database, or even creating users.
This functionality is, on the surface, similar to XML-RPC, but the REST API offers significantly broader capabilities. Additionally, application passwords are securely generated and are 24 characters long, so brute force and credential stuffing attacks are unlikely to be successful.
If you decide to make use of application passwords, we strongly recommend setting up a user with minimal permissions, ideally with only the necessary capabilities specifically for the application you wish to connect to.
The jQuery update continues
WordPress 5.5, released in August 2020, removed the jQuery Migrate script. This caused many sites using plugins dependent upon older versions of jQuery to experience issues.
If your site was affected and you’re currently using the Enable jQuery Migrate Helper plugin to work around these issues, you’ll want to make sure your site works without it before updating to WordPress 5.6.
This is because WordPress 5.6 will update to the latest version of jQuery and add jQuery Migrate 3.3.2, which can conflict with the version re-enabled by the Enable jQuery Migrate Helper plugin, which is jQuery Migrate 1.4.1.
WordPress has been using outdated versions of the jQuery library for several years now.
WordPress 5.6 is step 2 of a 3-step plan to get WordPress on an up-to-date version of jQuery. This plan has been:
Share This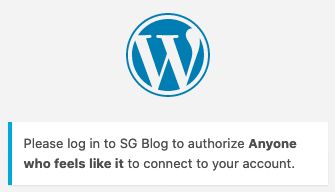





Be the first to comment